Logging with SSH Key
The clients that support the Secure SHell SSH port allow a secure connection to the login node. Only after a secure connection between the login node and the PC has been established, the PC sends our username and password to the login node. The biggest weakness of a secure connection is thus the user password; if it is too simple, an unauthorized person can guess the password and break into the system.
For this reason, cluster administrators prefer that we use an SSH key when connecting to the login node. An SSH key has two parts: a private and a public part. To log in using an SSH key, the public part must be installed on the login node.
Warning
The private part of the SSH key should not be shared with anyone, while the public part of the key can be shared with others.
After the login node receives the public part of our SSH key, it won't require a password anymore. Instead, it will send a simple challenge to the PC. The login node encrypts a random number using the public part of the SSH key and sends it to the PC. The PC decrypts the cypher using the private part of the SSH key and returns it to the login node. If the number matches, the connection will be established; otherwise, it won't.
Hint
For a more in-depth explanation of SSH encryption, see link.
Creating SSH Key
We open command line and write:
ssh-keygen -t ed25519 -C <label>
By using -t ed25519, we request the generation of a key using the EdDSA signature scheme, and with -C <label>, we can optionally add a label to the key for easier identification — for example, the name of the personal computer for which we want to create the SSH key. When prompted for the file to save the key and the passphrase to encrypt the private part of the key, press ↵ Enter.
Generating public/private rsa key pair.
Enter file in which to save the key (/home/user/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/user/.ssh/id_ed25519
Your public key has been saved in /home/user/.ssh/id_ed25519.pub
The key fingerprint is:
SHA256:xBjPXkGfSixhG4IBI7G/zfjClHcZMR2/a5OvGBEBV9s vm-ubuntu
The key's randomart image is:
+--[ED25519 256]--+
|o.o..o+oB++ |
| o .. oX.B = . |
|. .oO * E |
| . .o = o |
| .. oS o |
| o=. o . o |
| oo.o. . = |
| o. + o |
| .. . ... |
+----[SHA256]-----+
We have created an SSH key encrypted with the RSA algorithm, which is stored in two files: the private key is in the id_ed25519 file, and the public key is in the id_ed25519.pub file. The private key should not be shared with anyone, but the public key will be sent to the entry node.
Warning
Each time you execute the above command, a different key will be generated.
To display the public part of the SSH key, you can use the cat command on Linux and macOS, and the type command on Windows. Simply enter the full file name of the public key that was output by the previous command.
(Your public key has been saved in /home/user/.ssh/id_ed25519.pub).
$ cat /home/user/.ssh/id_ed25519.pub
cat /home/user/.ssh/id_ed25519.pub
The public part of the SSH key is displayed on the screen.
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFh0NIbjPmhcAhqMExbcVpshrPFIlj0QHfpp2/lUh1z1
If preferred, you can open the file in a text editor of your choice.
Distributing Public Part of the SSH Key
The Arnes, Vega, NSC, Maister and Trdina computer clusters use the FIDO system (Fast IDentity Online) for distributing the public part of the SSH key. To access all systems, we only need to publish the key in one place. When we log in to the entry node using an SSH client, the entry node in the FIDO system will verify if we have published the public part of the key and use it for authentication. If the key is not available, we will be prompted to enter a password.
To publish the public part of the SSH key, we first visit the website fido.sling.si.
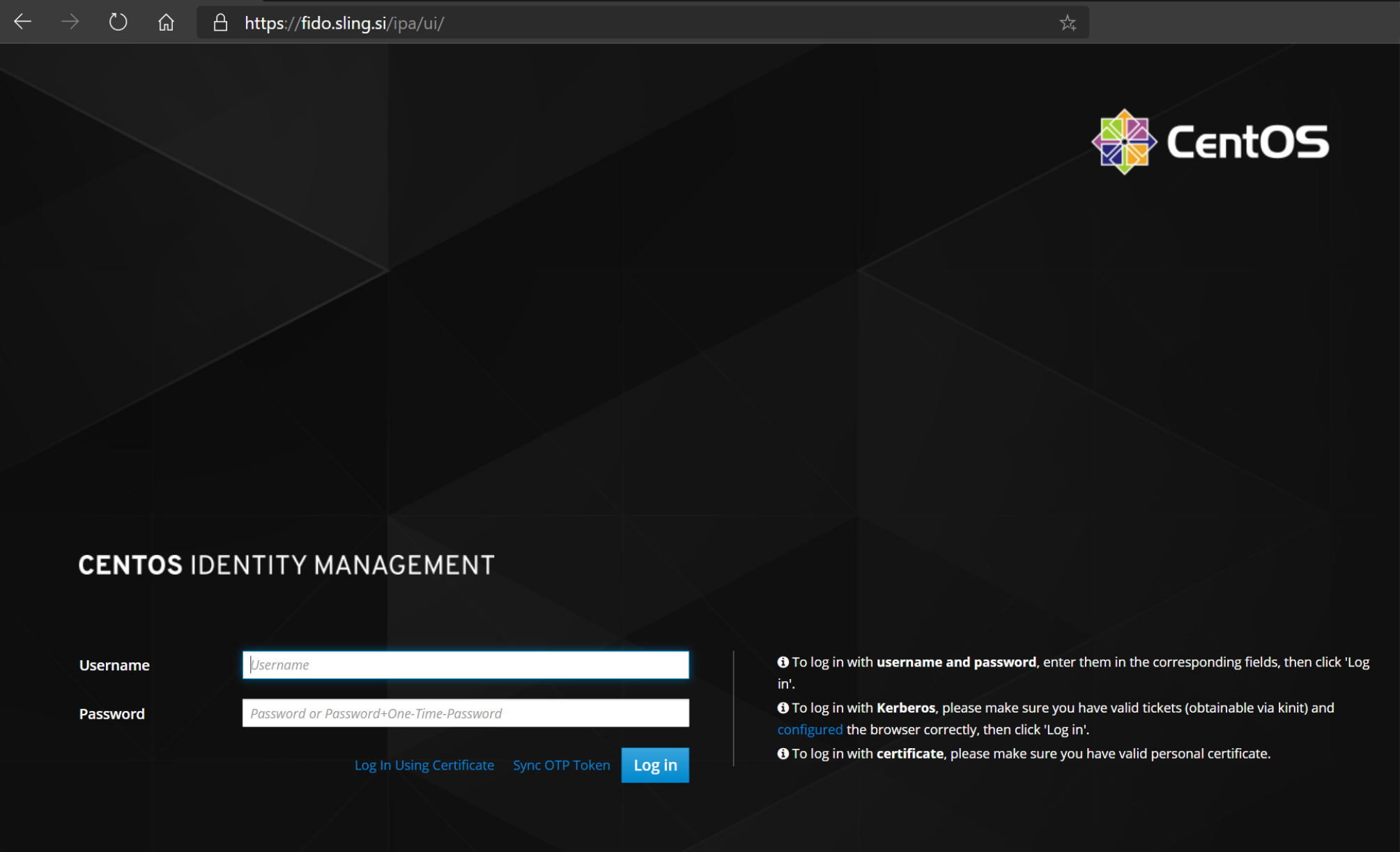
On login page sign in using your SLING SSO (Single Sign-On) credentials for accessing clusters. In the fields, Username and Password, we fill our username and password and press the button Login. After successful login, we can see the main page with our data.
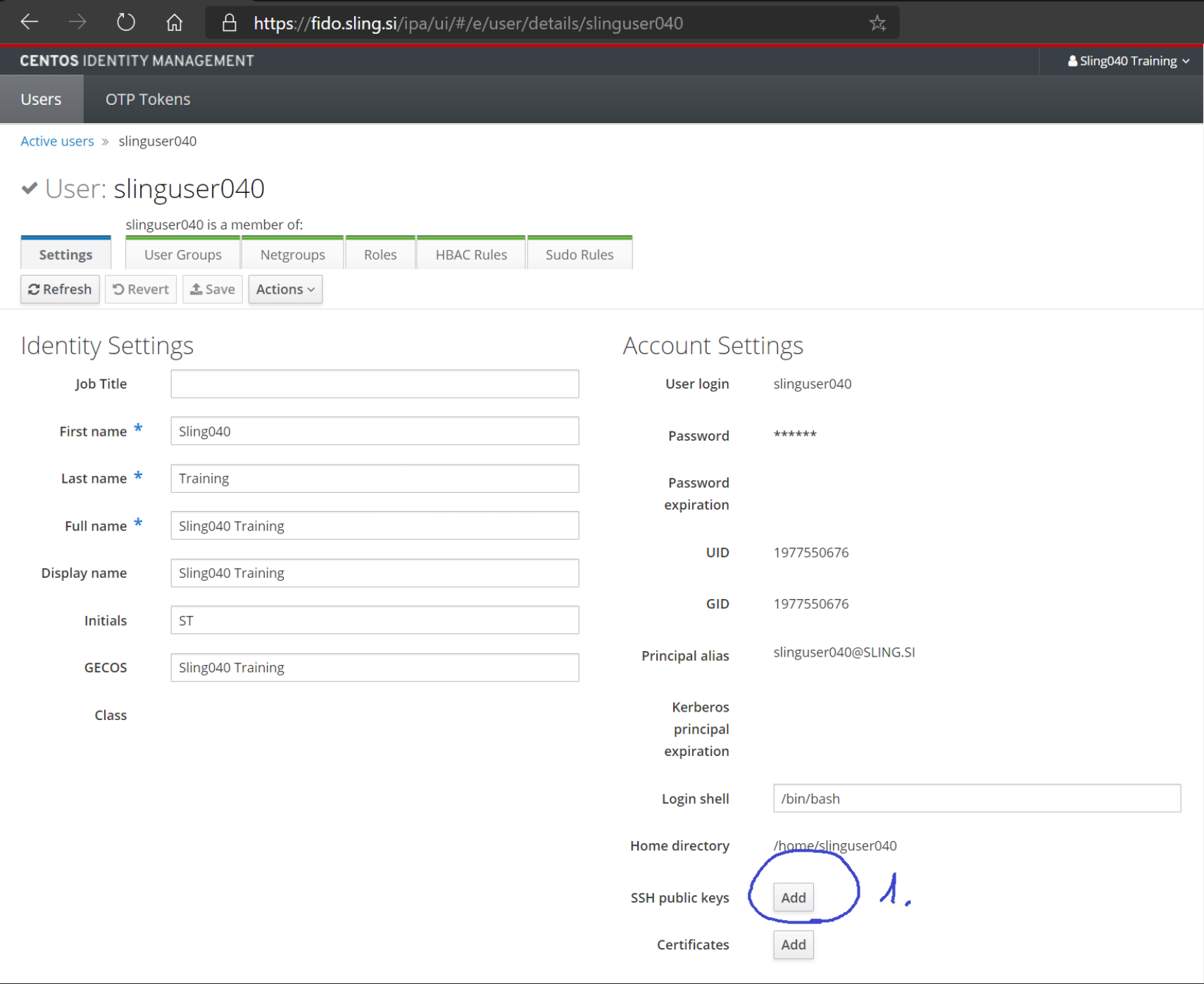
Look for the "Account Settings" section and locate the SSH public keys entry. Click on the Add button ( represented by Add label and circled with number 1).
A window or prompt will open, allowing you to enter the public part of your SSH key. You can copy the public key from your command line or a text editor and paste it into the provided field.
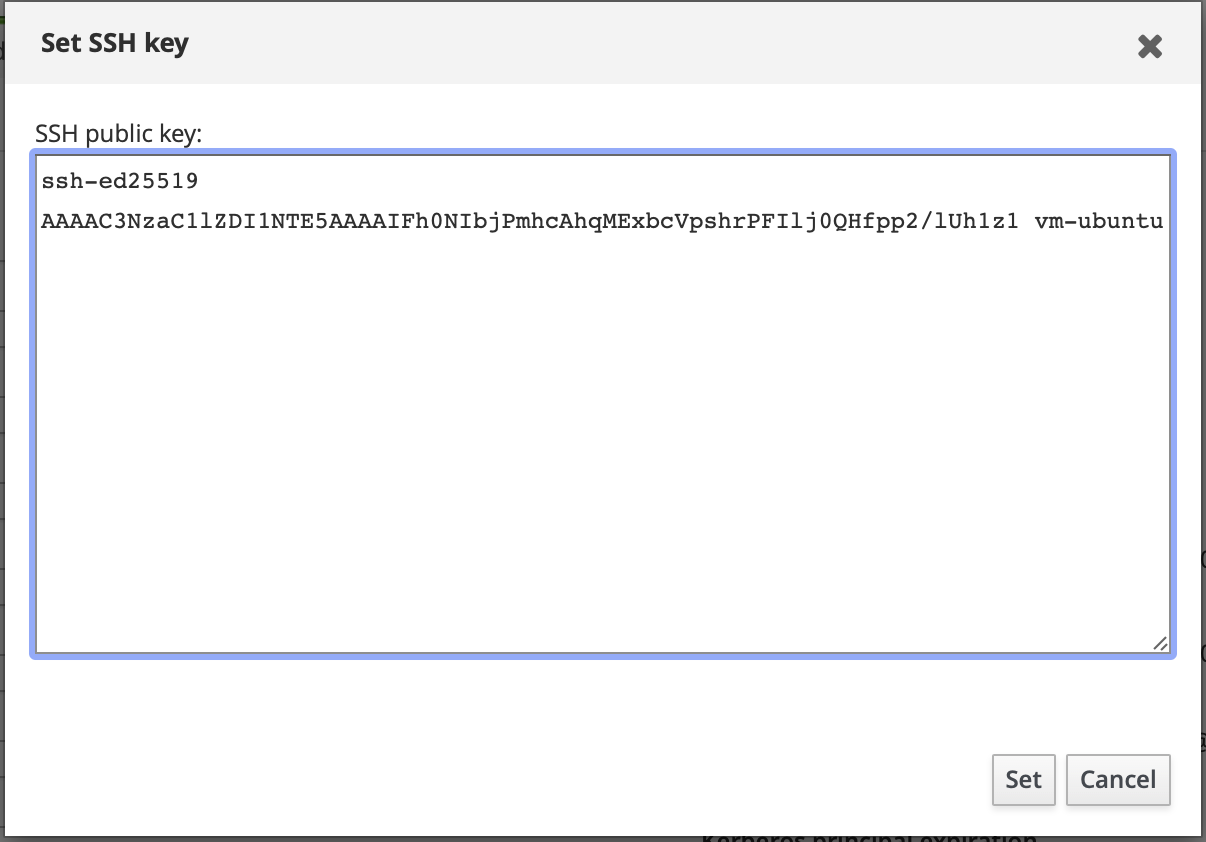
We click the button Set to close the window. After that, on the main page with our data, we press the Save button (the button is circled and labelled with the number 2). After saving the SSH public key, we can see it in the "SSH public keys" section (the public key is circled and labelled with the number 3). You can verify its presence by checking the "SSH public keys" section on the main page. The key should be listed there. Close the website or log out of your account.
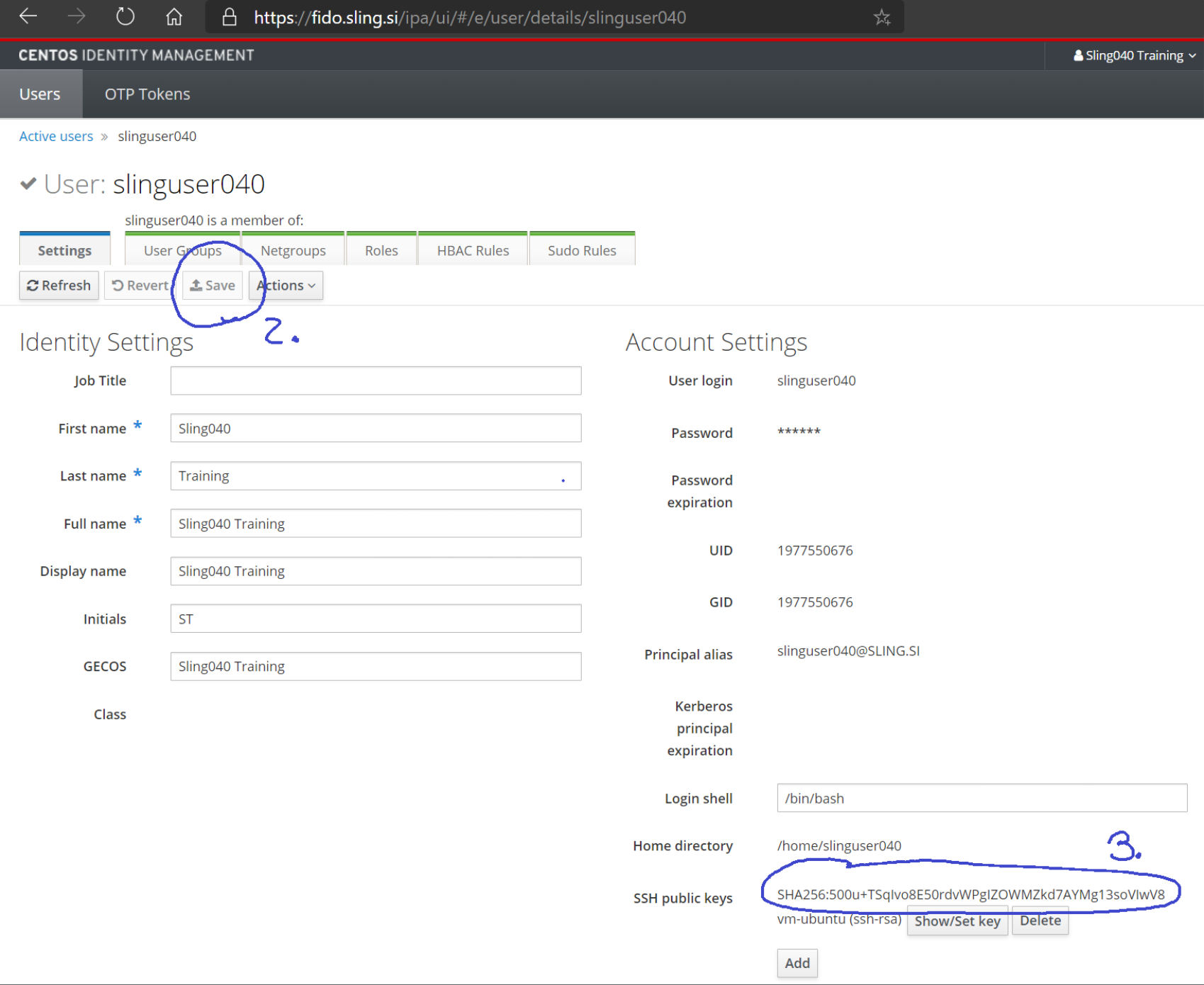
Close the website and try to connect to the login node without password. In command prompt we write:
$ ssh sling040@hpc-login1.arnes.si
Last login: Sat Jan 16 21:33:38 2021 from 93.103.18.69
ssh sling040@hpc-login1.arnes.si
Hint
For computer systems that are not integrated with SLING SSO, please follow the instructions specific to those systems. link.